Home >>
Samples >>
CYB 310 Network Defense >>
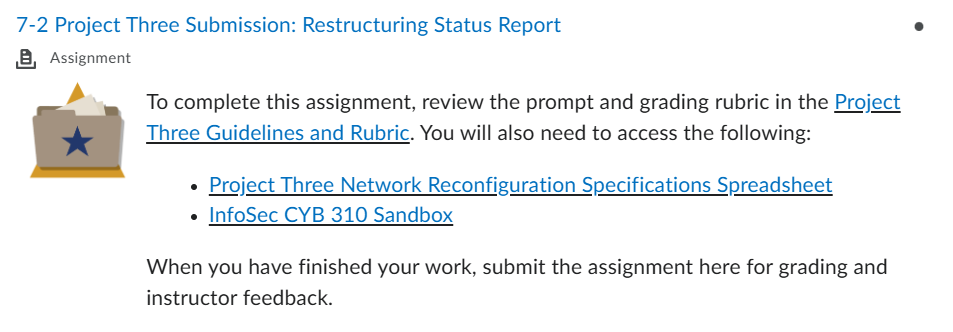
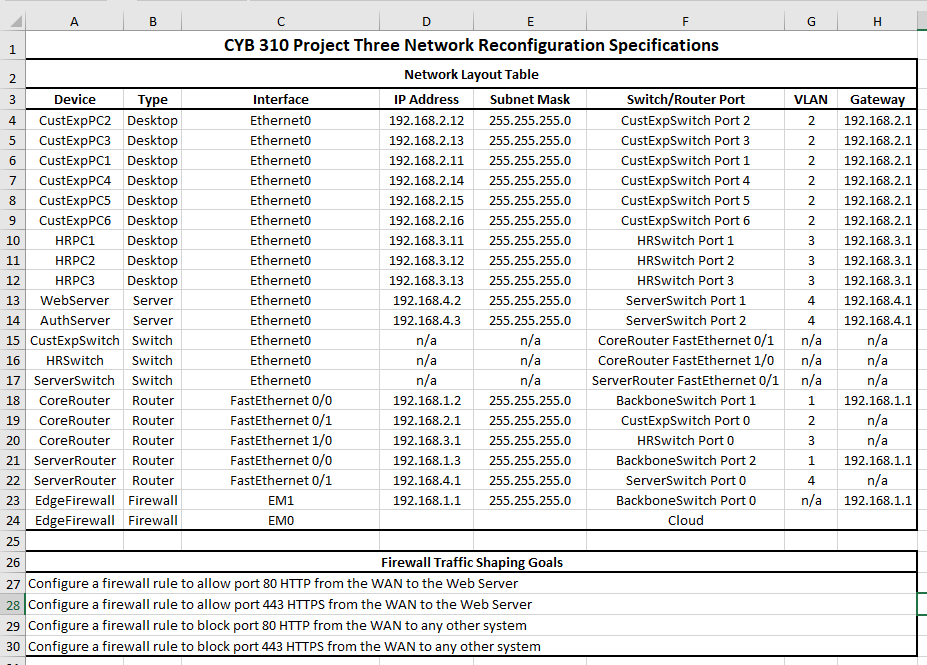
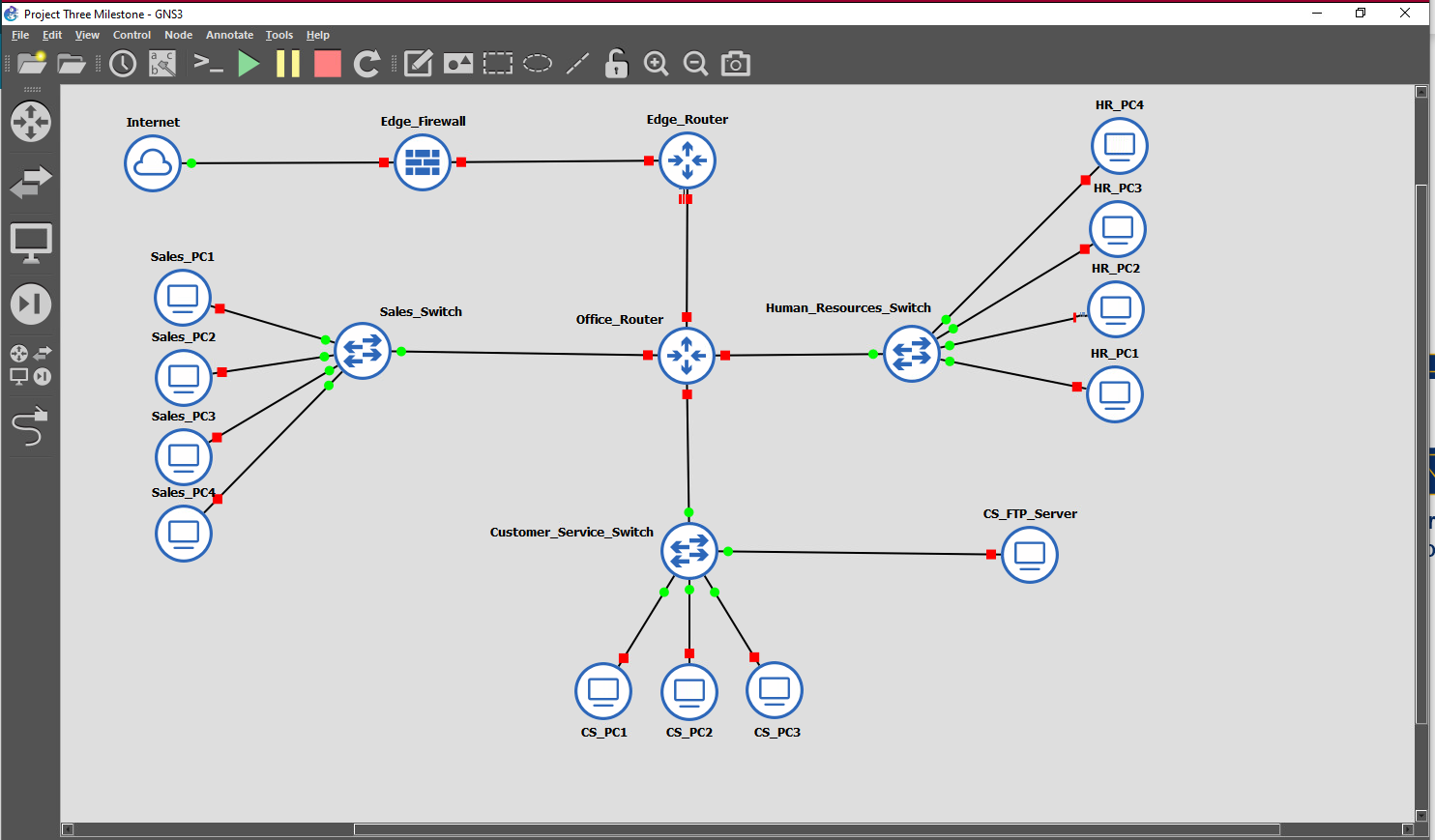
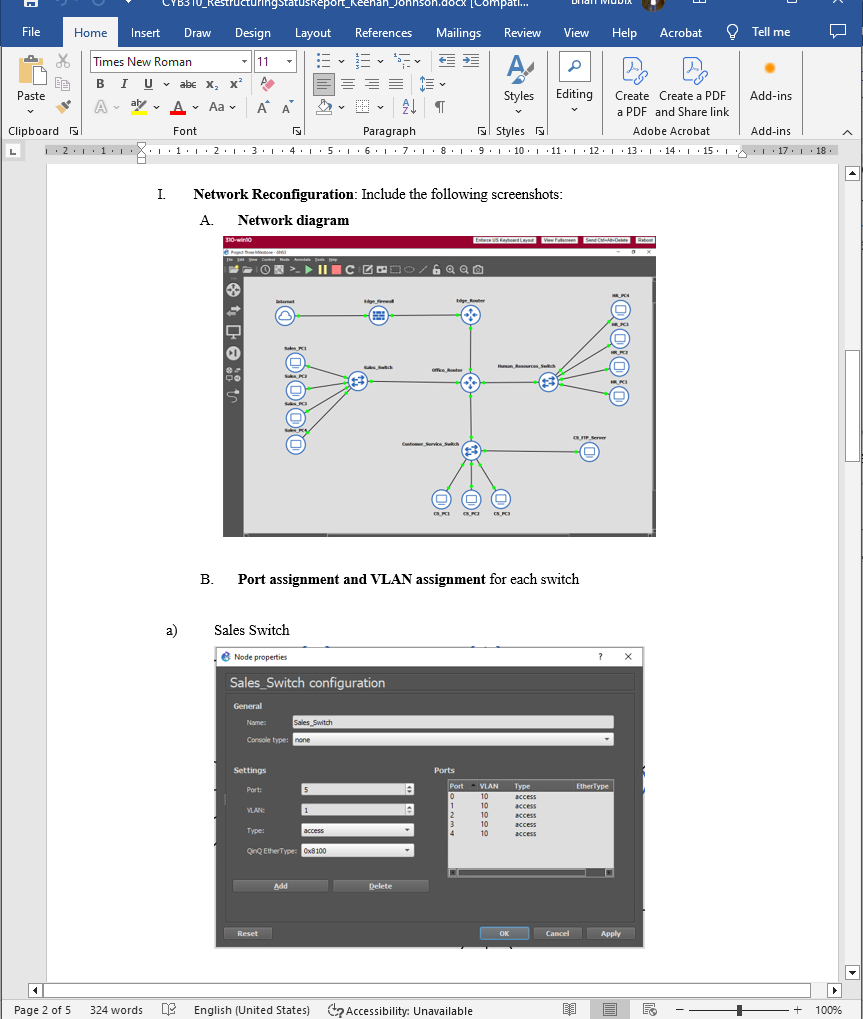
CYB 310: 7-2 Project Three Submission: Restructuring Status Report
Need your Own Custom Solution?
Order with full confidence and you will be amazed by our results
It’s pretty straightforward, but if you get stuck at any step, please feel free to contact us at any time for a chat.
WhatsApp support@gradegivers.com
NEED A UNIQUE PAPER ON THE ABOVE DETAILS?
Order Now
It’s pretty straightforward, but if you get stuck at any step, please feel free to contact us at any time for a chat.
WhatsApp support@gradegivers.com
NEED A UNIQUE PAPER ON THE ABOVE DETAILS?
Order Now
Place a Quick Order
Our verified writers got you covered. Let us help you balance between studies, work, and family.
Order NowRelated Questions
CYB 310: 8-2 Cyber Playbook Submission ...CYB 310: 8-1 Discussion: Managing Your Skill Set ...
CYB 310: 7-2 Project Three Submission: Restructuring Status Report ...
CYB 310: 7-1 Discussion: Firewall and Traffic Flow Policies ...
CYB 310 6-2 Project Two Submission: IDS Analysis Paper ...
CYB 310 : 6-1 Project One Submission: Network Evaluation Report ...
CYB 310 : 5-3 Project Three Milestone: Network Reconfiguration Pre-planning ...
CYB 310 : 5-2 Activity: Web Application Firewalls ...
CYB 310 : 5-1 Module Five Lab Worksheet Guidelines ...
CYB 310 : 4-3 Project Two Stepping Stone: Exploring IDS Best Practices ...