Introduction
This assignment assesses your understanding of the forecasting methods you have learned this week and gives you an opportunity to compare and evaluate the results of different forecasting methods.
Instructions
Submit your answers to all questions in a Word document. Download the data sets and use Excel to solve the problems.
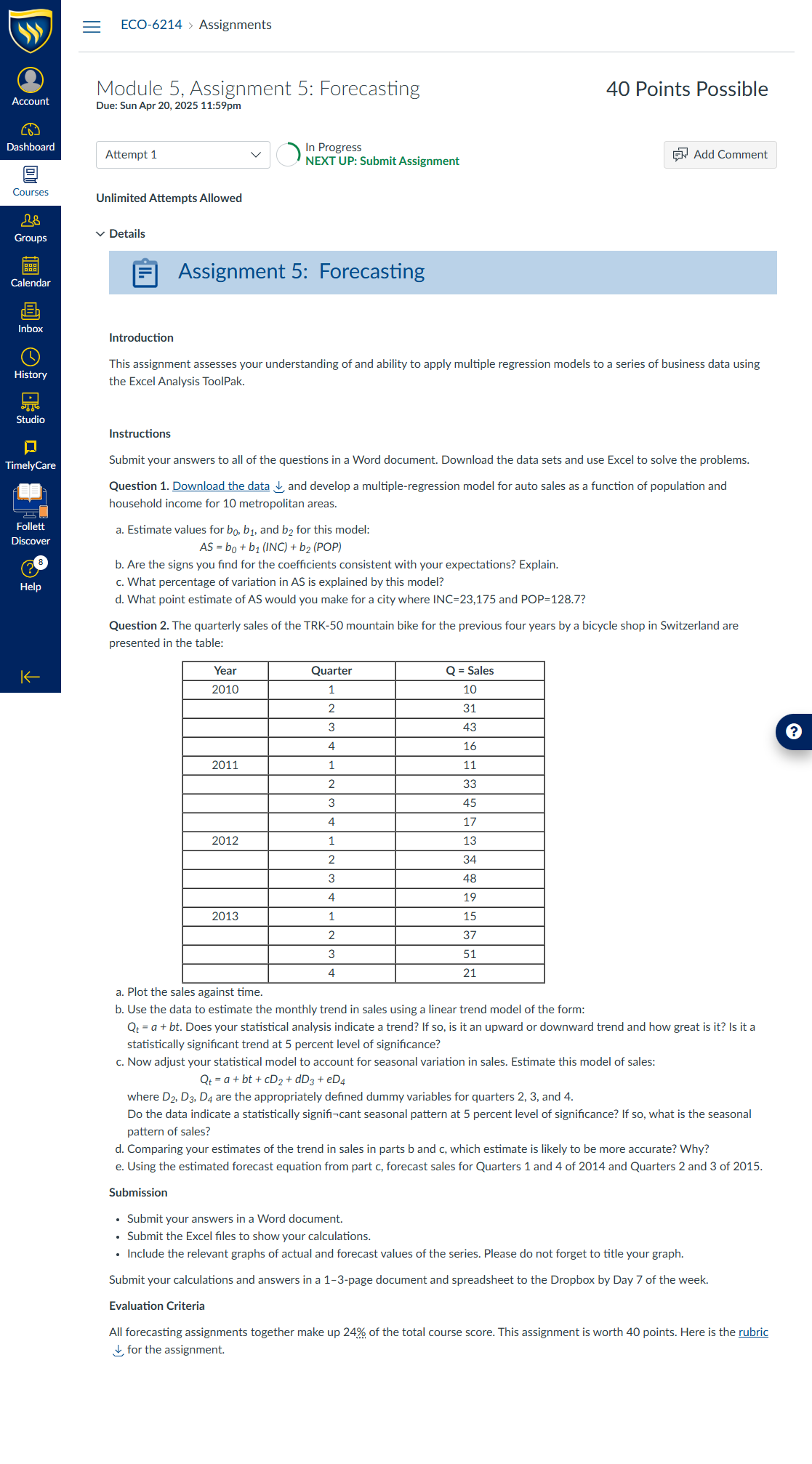
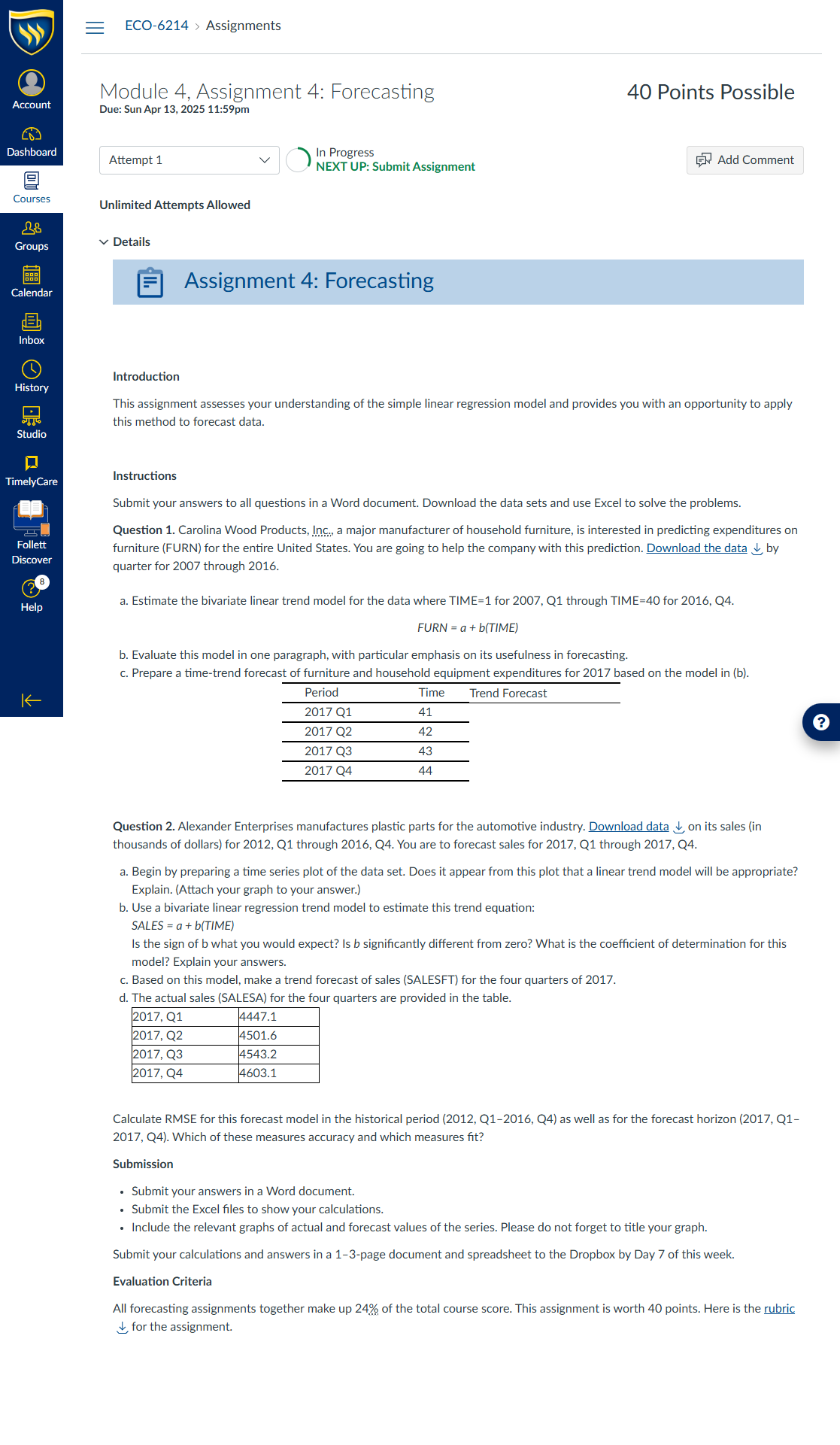
Question: Download the data on thermostat sales.
- Calculate both the three-month and the five-month averages for these data.
- Plot the data to examine the possible existence of trend and seasonality.
- Prepare the following two (2) separate forecasting models to examine the thermostat’s sales data using monthly data:
-
- An exponential smoothing model (α=0.38, smoothing constant for the level)
- Holt’s model (α=0.04, smoothing constant for the level; β=0.07, smoothing constant for the trend)
d. Examine the accuracy of the forecast given by each model ( four models: MA 3, MA 5, Simple Exponential smoothing and Holt's Method) by calculating the root mean square error (RMSE) for each during the historical period.
e. Which model does minimize the RMSE? Carefully explain which characteristics of the original data caused one of these models to minimize the RMSE.
f. Using Holt's method forecast 12 months of thermostat sales for 2017.
Hints:
Part e: In this task, you will calculate four Root Mean Square Errors (RMSE), one for each model (MA3, MA5, Simple Exponential Model, and Exponential Model with Trend-Holt’s Method). The MA3 and MA5 models are used to forecast stationary data (without trend). The Simple Exponential Model is used to forecast stationary data (without trend), while the Exponential Model with Trend-Holt’s Method is used to forecast non-stationary data (with trend).
Visualizing the data will help you detect any data patterns such as trend, seasonality, or stationary data with random errors. This will assist you in answering part e of the task.
Part f: In the lecture notes, the embedded video on Holt's Method did not explain how to forecast future data using Holt's Method. To forecast with Holt's Method, use the following algebraic form:
Ht+m = Ft+m * Tt
Here, Ht+m represents Holt’s forecast value for period t+m. Please watch virtual lab 3 recordings to learn how to complete this part.
Virtual Lab 3.
Assignment 3's dataset is larger than the previous assignments, and thus, you can limit the amount of data that you report in the Word document by following the instructions below:
Part A: Report a table that includes the last five periods of forecast (MA3 and MA5), including January 2017. Alternatively, you can include a plot of actual and forecast data.
Part B: Include a plot of actual data along with an explanation.
Part C: Report a table that includes the last five periods of forecast (Simple Exponential Smoothing and Holt's), including January 2017. Alternatively, you can include a plot of actual and forecast data. Please refer to the videos I posted to make a forecast with Simple Exponential Smoothing and Holt's.
Part D: Report the RMSE's of all four models.
Part E: Provide an explanation.
Part F: Include a table that shows a 12-month forecast with Holt's Method.
Submission
- Submit your answers in a Word document.
- Submit the Excel files to show your calculations.
- Include the relevant graphs of actual and forecast values of the series. Please do not forget to title your graph.
Submit your calculations and answers in a 1–3-page document and spreadsheet to the Dropbox by Day 7 of this week.